Could a single cyber incident disrupt your operations, damage your reputation, or shake client trust?
With cyber incidents in the financial sector increasing by over 50% in the past year alone, the risk is more real than ever. This makes it clear that relying solely on traditional security measures is no longer enough.
Organizations must now be prepared not only to prevent incidents but also to respond quickly and recover effectively.
The Digital Operational Resilience Act is designed to address precisely these challenges. It applies to banks, insurance companies, investment firms, payment services, crypto-asset providers, and even the ICT vendors that support them.
This DORA compliance ensures that financial institutions remain resilient even when unexpected disruptions occur by establishing clear rules for ICT risk management, DORA incident reporting, third-party oversight, and information sharing under DORA.
So, how can your organization navigate this complex DORA EU regulation without feeling overwhelmed?
In this blog, we will explore the 5 essential pillars of DORA compliance and provide a comprehensive DORA compliance checklist to guide your organization through the preparation process.
Let’s start by clarifying what DORA is and who it applies to!
Table of Contents
What Is DORA and Who Needs to Comply?
The Digital Operational Resilience Act (DORA) is a European Union regulation aimed at ensuring that financial entities can withstand, respond to, and recover from Information and Communication Technology (ICT)-related disruptions.
Effective from January 17, 2025, the DORA EU regulation introduces a comprehensive ICT risk management framework for financial entities, reinforcing operational resilience against cyber threats and ICT disruptions.
Who Must Comply?
DORA applies to a wide range of financial entities operating within the EU, including:
- Banks and Credit Institutions
- Investment Firms
- Insurance and Reinsurance Companies
- Payment and E-money Institutions
- Crypto-asset Service Providers
- Third-party ICT risk management vendors that supply critical services
Additionally, non-EU firms providing services to EU-based financial entities are also subject to DORA compliance.
What are the Objectives of DORA?
DORA aims to achieve the following objectives:
- Strengthen ICT Risk Management: Establishing robust frameworks for identifying, assessing, and mitigating ICT risks. Similar to HIPAA compliance in healthcare, it defines technical safeguards for protecting sensitive data.
- Ensure Incident Reporting: Implementing procedures for the timely reporting of significant ICT-related incidents.
- Conduct Resilience Testing: Regularly test ICT systems to ensure operational resilience.
- Oversee Third-party Risks: Managing risks associated with third-party ICT service providers.
- Facilitate Information Sharing: Promoting the exchange of information on cyber threats and incidents.
DORA improves the overall resilience of the financial sector and harmonizes how businesses manage ICT-related risks by guaranteeing structured DORA incident reporting and ICT risk management across EU institutions.
Unsure of your DORA compliance status but want to strengthen resilience and close compliance gaps?
To meet these objectives effectively, DORA defines 5 core pillars of compliance, which we will discuss now.
The 5 Essential Pillars of DORA Compliance
DORA’s compliance framework is defined by 5 key pillars that fortify the EU financial sector against digital disruptions. Each pillar focuses on a fundamental aspect of operational resilience, including:
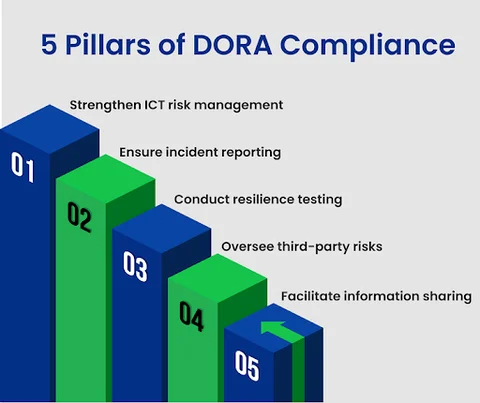
- managing ICT risks
- responding to incidents
- overseeing third-party service providers
- fostering information sharing across the industry
Organizations can develop a proactive approach to digital resilience by adhering to these pillars, which will guarantee quick recovery in the event of disruptions and help anticipate and mitigate potential threats. Sets the stage for a more secure, reliable, and collaborative financial ecosystem.
Let’s explore each pillar in detail!
1. ICT Risk Management Framework
Many financial institutions still rely on fragmented risk systems, outdated policies, and limited visibility into ICT threats, leaving them reactive rather than resilient.
What DORA Requires:
DORA mandates a comprehensive EU framework for ICT risk management that serves as the backbone of digital operational resilience and enables organizations to identify, assess, and mitigate ICT risks effectively.
It must define governance, assign ownership, monitor vulnerabilities, and continuously adapt to evolving cyber threats.
The Solution:
Organizations can build a proactive ICT risk management approach by:
- Mapping all critical ICT assets and assessing their business impact.
- Defining clear governance structures, with CISOs or CIOs owning ICT risk accountability.
- Automating monitoring through centralized dashboards for real-time alerts.
- Updating risk registers quarterly to include new threat vectors.
| Key Elements | Resulting Benefit |
|---|---|
| Define governance and assign ownership | Faster risk escalation & decision-making |
| Conduct regular risk assessments | Early identification of vulnerabilities |
| Embed ICT risk into daily ops | Operational resilience & regulatory readiness |
| Continuous monitoring | Reduced downtime and security breaches |
For Example:
A bank conducting quarterly vulnerability assessments and automated patch management reports 40% fewer service disruptions (European Banking Authority).
2. Incident Reporting and Classification
Organizations often lack a unified process for detecting, classifying, and reporting ICT incidents quickly. This leads to delays, missed reporting windows, and potential non-compliance.
What DORA Requires:
DORA enforces structured incident management, including classification by severity and the mandatory reporting of major ICT incidents to regulators within 24 hours.
The Solution:
Establish a clear Incident Response Framework with the following:
- Predefined classification matrix (e.g., minor, significant, critical).
- Automated detection tools that trigger internal alerts.
- Regulatory reporting workflows to submit incident details within 24 hours.
- Post-incident reviews to strengthen future responses.
Example:
If a payment processor experiences a significant outage, it logs and classifies the event, informs regulators within 24 hours, and updates its response protocol based on the root cause.
Key Outcome:
Faster detection, compliance with reporting timelines, and improved organizational trust with regulators.
3. Digital Resilience Testing
Most institutions assume their backup and recovery plans will work until they don’t. Without regular testing, resilience gaps often go unnoticed until an incident occurs.
What DORA Requires:
DORA mandates periodic digital resilience testing (aligned with ENISA standards), including Threat-Led Penetration Testing (TLPT) for high-impact systems.
The Solution:
Implement a structured Resilience Testing Program that includes:
- Annual vulnerability assessments for infrastructure and apps.
- TLPT simulations that mirror real-world attack scenarios.
- Backup restoration drills to validate recovery times (RTO/RPO).
- Actionable test reports feeding directly into the ICT risk register.
Example:
A European investment firm conducts TLPT annually, uncovering API vulnerabilities before attackers can exploit them, saving millions in potential downtime.
Key Outcome:
Data-driven readiness, faster recovery capability, and measurable resilience maturity.
4. Third-Party ICT Risk Management
Outsourced services introduce high dependencies and hidden vulnerabilities. For SMEs and startups, vendor resilience often isn’t evaluated beyond cost and convenience.
What DORA Requires:
DORA demands full accountability for outsourced ICT services, including due diligence, contractual oversight, continuous monitoring, and contingency planning.
The Solution:
Adopt a Vendor Risk Management Lifecycle covering:
- Vendor risk scoring before onboarding.
- Contractual clauses enforcing DORA-aligned obligations.
- Ongoing performance reviews and independent audits.
- Contingency plans for critical vendor failures.
Example:
A fintech startup using a cloud storage vendor implements a DORA-aligned third-party monitoring tool to track uptime, audit logs, and recovery performance.
SME Tip:
Even smaller vendors should maintain basic resilience documentation, including backup procedures, security certifications, and response timelines.
Key Outcome:
Minimized vendor-related disruptions and a transparent, accountable supply chain.
5. Information Sharing and Collaboration
Many organizations operate in isolation, missing valuable intelligence that could prevent large-scale incidents. Lack of structured information sharing increases systemic risk across the sector.
What DORA Requires:
DORA promotes sector-wide collaboration through structured information sharing to build collective defense.
The Solution:
Develop an Information Sharing Strategy that includes:
- Participation in trusted networks like FS-ISAC, ECSO, or ENISA.
- Automated threat intelligence platforms (TIPs) for real-time sharing.
- An anonymized data exchange that respects privacy laws (GDPR).
- Joint response exercises with partners and regulators.
Example:
A European bank shares phishing patterns on the ENISA platform; peers quickly update filters and avoid similar breaches.
Key Outcome:
Collaborative resilience, such as reducing incident frequency and enhancing sector-wide defense readiness.
| Pillar | Challenge | Solution / Key Actions | Outcome |
|---|---|---|---|
| ICT Risk Management | Fragmented risk visibility | Define governance, automate monitoring, and update the risk register | Fewer disruptions |
| Incident Reporting | Delayed detection & reporting | Classify, log, and report incidents within 24h | Faster response & compliance |
| Resilience Testing | Unverified recovery plans | Conduct TLPT & backup recovery drills | Proven system resilience |
| Third-Party Risk | Vendor dependency & blind spots | Enforce DORA-aligned vendor contracts, audit quarterly | Reduced external risk |
| Information Sharing | Isolated threat visibility | Join FS-ISAC/ENISA networks for active sharing | Collective defense strength |
How Can Your Organization Prepare for DORA Compliance Step by Step?
Preparing for DORA compliance may seem overwhelming at first. There are many rules, frameworks, and technical terms, and it’s easy to feel lost. Compliance is making your organization stronger, smarter, and ready for whatever digital challenges may come.
However, the goal goes beyond satisfying regulators. It is about protecting your systems, your customers, and your reputation. By following a structured approach, you can identify gaps, strengthen processes, and build confidence that your organization can handle disruptions efficiently.
How do you actually get there? Let’s break it down step by step in a way that feels practical and achievable.
1. Assess Your Current Digital Resilience
Before you can improve, you need to know where you stand. Start by evaluating your current systems, processes, and policies with the help of Cloud & DevOps Services.
Ask yourself:
- Which critical ICT systems are most vulnerable?
- Do we have documented incident response plans?
- Are recovery times realistic for potential disruptions?
This step helps you identify gaps that DORA requires you to address, from operational resilience to cyber risk management.
2. Strengthen Risk Management Practices
Once weaknesses are identified, it’s time to reinforce them. Focus on practices that actively reduce risk.
- Conduct regular risk assessments and stress tests.
- Document all ICT-related risks and mitigation plans.
- Ensure continuous monitoring of critical systems.
These measures not only meet DORA’s expectations but also help your organization prevent issues proactively.
3. Test and Improve Incident Response
Responding to disruptions quickly is as important as preventing them. Prepare your team by:
- Conducting digital resilience tests, including simulated cyber incidents.
- Establishing clear communication channels during incidents.
- Training staff on their roles and responsibilities in incident response.
Think of it as a fire drill, but for your digital systems. The more realistic your practice, the smoother the response will be in a real event.
4. Manage Third-Party ICT Risks
Many disruptions happen because of third-party providers. DORA requires financial organizations to manage these risks actively:
- Keep an up-to-date inventory of all critical ICT third parties.
- Conduct regular audits and assess their operational resilience.
- Include contingency plans for third-party failures in your internal policies.
By knowing your partners’ strengths and weaknesses, you reduce the chance of being blindsided by an external issue.
5. Document, Monitor, and Report
Finally, DORA expects financial organizations to document their processes and monitor compliance continuously:
- Maintain detailed records of risk assessments, testing, and incident responses.
- Regularly review policies and update them as systems evolve.
- Prepare reporting frameworks to meet regulatory expectations efficiently.
This step ensures transparency, accountability, and ongoing improvement, so compliance becomes a natural part of your organization’s routine.
A Complete Checklist to Check DORA Readiness of Your Organization
Use this checklist to evaluate your organization’s readiness for DORA compliance. Tick off each question to identify strengths and areas that may need improvement.
| Sr. No. | Question | Status | |
|---|---|---|---|
| 1 | Are our current digital systems resilient enough? | ☐ | |
| 2 | Are our risk management practices solid? | ☐ | |
| 3 | Can we respond to incidents effectively and quickly? | ☐ | |
| 4 | Are third-party ICT risks properly managed? | ☐ | |
| 5 | Are our documentation and reporting processes up to standard? | ☐ | |
| 6 | Do we have timely incident reporting procedures? | ☐ | |
| 7 | Are we actively testing and improving digital resilience? | ☐ | |
| 8 | Are third-party disruptions minimized? | ☐ | |
| 9 | Are we sharing threat intelligence effectively? | ☐ |
Once these steps are in place, your organization will be closer to DORA compliance and more resilient against unexpected digital disruptions.
Frequently Asked Questions (FAQs)
2. What Are The Key Pillars Of DORA Compliance?
- ICT risk management
- Incident reporting and classification
- Digital resilience testing
- Third-party ICT risk management
- Information sharing under DORA
Together, they ensure organizations can respond effectively to digital disruptions.
3. How Should Third-Party ICT Providers Comply With DORA Requirements?
Outsourced ICT providers should align with the organization’s resilience policies, undergo regular audits, assess service reliability, and maintain clear contracts outlining responsibilities for third-party ICT risk management.
4. What Methodologies Are Recommended For Digital Resilience Testing Under DORA?
Recommended digital resilience testing methods include vulnerability assessments, threat-led penetration testing, and recovery exercises. These ensure both technology and teams are prepared for operational disruptions.
5. How Does Dora Compliance Differ From Other Regulations Like GDPR or NIS2?
Key differences include:
- Focus on operational resilience specifically for financial entities
- Integration of ICT risk management and DORA incident reporting
- Management and oversight of third-party ICT providers
- Promotion of sector-wide information sharing under DORA
6. What Are The Penalties For Non-Compliance With DORA?
Firms that fail to comply with DORA can face significant administrative fines, restrictions on business operations, or even suspension of certain activities. Beyond the financial implications, non-compliance can severely damage credibility and client trust, especially in a sector where operational resilience and data integrity are critical.
7. How can EU financial firms ensure third-party vendors meet DORA standards?
Under DORA, financial entities must take responsibility for their third-party ICT providers. This means conducting due diligence, monitoring vendor risk, and ensuring contractual agreements clearly define security, reporting, and incident response requirements. Regular audits and risk assessments are key to ensuring alignment with DORA’s expectations.
Conclusion: Strengthen Your DORA Readiness
DORA compliance can feel overwhelming at first, but it is an essential step toward making your organization stronger and more resilient. The 5 DORA pillars can help you develop a clear operational resilience roadmap.
To turn these pillars into action, the DORA Readiness Checklist ties all pillars together. It allows you to see where your organization stands. It highlights gaps that need attention. It gives you practical steps to improve systems and processes. Completing the checklist makes DORA compliance actionable instead of abstract.
Additionally, the Digital Transformation services can expedite the process. These services support organizations in modernizing systems, improving incident response, and building resilience across internal processes and third-party partnerships. They make it easier to implement the DORA pillars and complete the checklist effectively.
Ultimately, preparing for DORA is about building confidence, reducing risks, and being ready for unexpected digital challenges. Your company can become more secure, resilient, and future-ready by implementing Digital Transformation services, using the checklist, and adhering to the five pillars.
Are gaps in your ICT systems or third-party risks putting your operations at risk?







Share your thoughts about this blog!